Processing agreement
Comprised of:
Part 1. Data Pro Statement
Part 2. Standard Clauses for Data processing
Part 1: Data Pro Statement
Along with the Standard Clauses for Data Processing, this Data Pro Statement constitutes the data processing agreement for the product or service provided by the company that has drawn up this Data Pro Statement.
General information
-
This Data Pro Statement was drawn up by the following Data Processor:
CDD Solutions B.V.
Hillegomstraat 12-14 units: 1.02
1058 LS Amsterdam
The Netherlands
If you have any queries about this Data Pro Statement or data protection in general, please contact:
By email: info@cddsolutions.com
By phone number: +31 (0) 85 489 1829
By mail: CDD Solutions B.V. Hillegomstraat 12-14 unit 1.02, 1058 LS Amsterdam
-
This Data Pro Statement shall enter into force on March 2023
We regularly revise the security measures described in this Data Pro Statement to ensure that we are always fully prepared and up to date with regard to data protection. If this document is updated, we shall notify you of the revised versions through our regular channels.
-
This Data Pro Statement applies to the following products and services provided by data processor
- Complete Software as a Service compliance information system including - but not limited to – an automated sanction checker, transaction monitoring module and client acceptance module.
- CDD Solutions projects & support environnement.
-
Description of Complete Compliance Information System
The complete SaaS compliance information system is an online compliance application designed for all financial organizations and AML/CFT mandatory institutions to meet their KYC/CDD obligations. The functionalities of the software have been developed for all gatekeepers of the financial system. The software supports organizations with their client acceptance, client management and transaction monitoring. Besides, the complete compliance information system consists of an automated sanction checker.
-
Description of CDD Solutions projects & support environment
Our projects & support environment enables our clients to request and receive support for products and services CDD Solutions supplies.
-
Intended use of CDD Solutions Complete Compliance Information System
The Complete Compliance Information System was designed and built to process the following types of data: complete compliance dossiers consisting of client acceptance forms, business relations, transactions,
When this product/service was designed, the possibility that it would be used to process special categories of personal data or data regarding criminal convictions and offences was not taken into account. It is up to client to determine whether or not it shall use the aforementioned product or service to process such data.
-
Intended use of CDD Solutions projects & support environment
The projects & support environment was designed and built to process the following types of data: client support requests and internal project management information.
When this product/service was designed, the possibility that it would be used to process special categories of personal data or data regarding criminal convictions and offences was not taken into account. It is up to client to determine whether or not it shall use the aforementioned product or service to process such data.
-
When data processor designed the product or service, it applied a privacy-by-design approach in the following manner:
Clients upload their data themselves, including attachments chosen by them, and can access them change and delete data and documents. The processor does not check the data and will only view data on request of the client, for example if this is necessary to help answer a support request.
-
Data processor uses the Data Processing Standard Clauses for data processing, which are attached to the Agreement as an addendum.
-
CDD Solutions shall process the personal data provided by its clients within the EU/EEA.
-
Data processor uses the following sub-processors:
- Amazon Web Services, Inc. provides hosting for our services and processes all our data within the EU/EEA. We have concluded a data processing agreement with AWS, their privacy statement can be found at the following location: https://aws.amazon.com/privacy/
- Toccata B.V. provides administrative services and processes all our data within the EU/EEA. We have concluded a data processing agreement with Toccata, their privacy statement can be found at the following location: https://toccata.nl/terms/privacy/
- Salt Edge Limited provides access to open banking data and account information. By using our Transaction Monitoring module, you acknowledge and agree that your use of open banking and account information is subject to Salt Edge's End-user Dashboard Terms of Service and End-user Dashboard Privacy Policy. Please review Salt Edge's Terms of Service ( https://www.saltedge.com/dashboard/terms_of_service) and Privacy Policy ( https://www.saltedge.com/dashboard/privacy_policy) for details on how they handle your personal information and for your rights and obligations when using this service.
-
Data processor shall support its clients in the following way when they receive requests from data subjects:
Data subjects may access and rectify their personal data via their profile page on each of our services. For erasure of personal data, unless storage is required by law, please contact us.
-
Once an agreement with a client has been terminated, data processor shall delete personal data it processes on behalf of client within three months, in such a manner that they shall no longer be able to be used and shall be rendered inaccessible.
The account of the user will be terminated and all data associated with this account will be removed within three months.
Security policy
-
Data in transit protection
Data transmitted between CDD Solutions clients and the CDD Solutions service uses the Hypertext Transfer Protocol Secure (HTTPS) which secures data using TLS (Transport Layer Security). Data routed through the public internet is never transmitted without encryption.
Additionally, our services are mutually authenticated. The user authenticates to the service with an e-mail, password and optionally two-factor authentication. The CDD Solutions service is authenticated by the user’s web browser using a TLS certificate.
-
Asset protection and resilience
-
Physical location and legal jurisdiction:
Customer data resides in our Amazon Web Services (AWS) production environment, physically located within European AWS data centers. CDD Solutions may access customer data:
- In the event of a system malfunction it may be required to access customer data in order to determine the cause of the problem.
- Sometimes we provide support to the customer which requires access to their data. This only occurs at the request of the customer.
- We may analyse customer data in order to improve our services. For example, by analysing trends for search engine optimization or by using machine learning.
-
Data center security:
Customer data resides in our AWS production environment. Physical protections are entirely provided by AWS, which has a wide range of security certifications to its physical security. More data on AWS data center security can be found here. -
Data encryption:
Data at rest, such as relational databases, file stores and database backups are encrypted. AWS Key Management Service (KMS) is used for managing encryption keys. -
Data sanitization and equipment disposal
Customers can remove their data from the application at any time. When they choose do this, CDD solutions ensures that the data is removed from the database. An exception is that the user can currently not delete their own organization and/or user account. If they wish to do so, they can contact support with their request.
The hosting provider (AWS) is responsible for ensuring removal of data from disks allocated to CDD Solutions use before they are repurposed. Furthermore, they are responsible for ensuring that equipment is disposed of in a responsible manner. More info on AWS processes for sanitizing data can be found here. -
Physical resilience and availability:
CDD Solutions creates backups of all production data. These backups are stored in Amazon S3 which is designed to store data durably. This is accomplished by replicating the data over multiple physical locations separated by a meaningful distance of many kilometres.
-
Physical location and legal jurisdiction:
-
Separation between customers
CDD Solutions is hosted in an Amazon Web Services Virtual Private Cloud and uses a multi-tenant solution where data is logically separated. Logical separation ensures that customers can only access their own data and no one else’s.
-
Operational security
-
Vulnerability management
CDD Solutions strives to keep software dependencies up to date to mitigate the risk of security vulnerabilities. Automated tools are in place to inform us in the case that a software dependency contains a known security vulnerability. If a security vulnerability is found, the severity and impact are investigated such that the appropriate action can be taken. Furthermore, tools are used that analyse the software that we create and identifies any potential security problems. -
Protective monitoring
CDD solutions has comprehensive monitoring in place which monitors the availability of the system, the health of its various components (such database, web servers and caching) and abnormal situations such as software errors. -
Configuration and change management
Tools and policies are in place which require that changes in our software and configurations are first reviewed and tested by another employee before these changes are deployed.
CDD Solutions’ hosting provider, Amazon Web Services (AWS), is responsible for patching and fixing flaws within the infrastructure, as well as maintaining the configuration of its infrastructure devices. For more information, please see AWS’s Shared Responsibility Model.
-
Vulnerability management
-
Personnel security
CDD solutions ensures that a background verification is performed on for all people working at CDD Solutions. These activities are performed within the legal limits of the local jurisdiction.
The concept of least privilege is applied to all CDD Solutions systems as they are all able to scope permissions. Access to customer data is restricted specifically to a select group of privileged engineers. In the event that an employee is terminated or leaves, CDD Solutions revokes all system access as soon as possible.
-
Secure development
Code complexity increases the chance of security issues. CDD Solutions makes use of internal code reviews, linting tools, code security tools and automated tests to ensure the quality of the code, so it can be extended and maintained effectively. CDD Solutions strives to keep software dependencies up to date to mitigate the risk of security vulnerabilities. Development environments are password protected and encrypted using full disk encryption. CDD Solutions’ code repositories are protected using two-factor authentication. Passwords are stored securely in a password manager.
-
Supply chain security
CDD Solutions’ subprocessors (external providers that process customer data) are carefully selected with security in mind. AWS is ISO/IEC 27001:2013 certified and is at least audited annually.
-
Secure user management
Customers are responsible for managing members, groups, roles and assignments of their organization within the CDD Solutions application. This application uses the role- and resource- based access control (RRBAC) which is a common approach to restricting system access to authorized users.
-
Identity and authentication
The CDD Solutions applications requires authentication by password. It enforces requirements on user passwords aiming to prevent the user from setting a weak password. However, ultimately these mechanisms cannot guarantee a secure password and therefore users are responsible for this themselves. For an added layer of security, users can (and are encouraged to) setup two-factor authentication (2FA).
-
External interface protection
The services are available to the user via an internet exposed web application. No API which exposes user data currently exists. This web application uses authentication as explained in section 9. Furthermore, these services are protected against the most common and frequently occurring network and transport layer DDoS attack by AWS. See AWS Shield documentation for more information.
-
Secure service administration
Different interfaces are used to perform service administration. These interfaces are protected with password and two-factor authentication and are designed such that they do not expose more information to the employee then required in order to perform the administrative task such as invoicing and customer management.
In the case of highly privileged administration interfaces, additional security measures are in place. More specifically, server administration is performed through a Bastion Host which is only accessible from a limited set of IP-addresses and is protected with public/private key authentication and two-factor authentication.
-
Audit information and alerting for customers
The CDD Solutions application logs various modifications in the user data. These modifications can be viewed by customers within the application’s audit log.
-
Secure use of the service
CDD Solutions offers several security features that can optionally be configured by the user depending on their security requirements. This includes two-factor authentication which adds an extra layer of authentication. Furthermore, a sophisticated access control system is provided based on the role- and resource- based access control (RRBAC). This allows for compartmentalising of resources and restricting access to a limited group of users.
Data leak protocol
-
In the unfortunate event something does go wrong. CDD Solutions shall follow the following data breach protocol to ensure that clients are notified of incidents:
Reporting a data breach
Customers and other external parties can report a security incident or possible data breach as soon as possible to contact@cddsolutions.com or by phone +31 (0) 85 489 1829. When a customer or other external party reports a security incident or a possible data breach the following information should be reported as soon as possible:
- The contact information, including an email address and/or phone number, of the reporter
- The nature of the data breach or security leak
- All information needed to reproduce and/or investigate the data breach or security leak
A report of a data breach should include the following information:
- The nature of the infringement
- The cause of the data breach
- A description of the leaked personal data
- Any measures that have been or are being taken to close the data breach
- An assessment of the risk that those involved may run
- How those involved have been informed about the data breach and its consequences for those involved
- Whether or not the Dutch DPA has been informed and the reasons why
CDD Solutions registers every report and, if necessary, contacts the reporter to obtain additional information.
Assessment of a data breach report
When a data breach report is received it should be assessed as soon as possible, within a maximum of 72 hours. The assessment of the report and as to whether to report to the Dutch DPA is based on the “Data Breach Notification Obligation Policy” defined by the Dutch DPA. This document can be found at the following location: https://autoriteitpersoonsgegevens.nl/sites/default/files/atoms/files/policy_rules_data_breach_notification_obligation.pdf
Figure 1 shows the assessments to be taken when a data breach is reported.
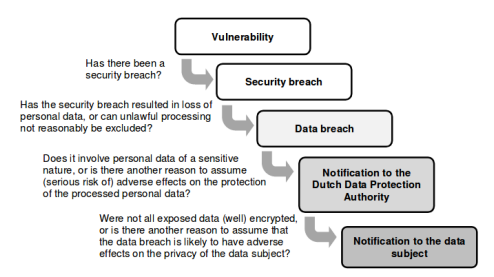
Figure 1 - Data breach assessment flowchart Data breach
One can only speak of a data breach when an actual security breach has occurred. A security breach may, for example, be the loss of a USB-key, the theft of a laptop or intrusion by a hacker. However, not every security breach comprises a data breach. A security breach is considered to be a data breach if it involves the loss of personal data, or if unlawful processing of personal data cannot reasonably be excluded. If there is only a weak spot in security, we speak of a vulnerability or a security incident and not of a data breach.
Notifications to the Dutch DPA
A security breach without data breach does not have to be reported to the Dutch DPA. Also not every data breach has to be notified to the Dutch DPA. By law, we are required to notify the Dutch Data Protection Authority if the data breach leads to a considerable likelihood of serious adverse effects on the protection of personal data, or if it has serious adverse effects on the protection of personal data. One of the factors that play a role here is the nature of the exposed personal data. If these concern personal data of a sensitive nature, then in general a notification is required. Examples of personal data of a sensitive nature are:
- Special personal data as provided in article 16 Dutch Data Protection Act. This includes personal data about a person’s religion or belief, race, political opinions, health, sexual life, membership of a trade union, as well as criminal personal data and personal data relating to unlawful or objectionable behavior in connection with a restraining order imposed in connection with such behavior.
- Data about the financial or economic situation of the data subject. This includes for example data on (problematic) debts, salary or payments details.
- (Other) data which may lead to stigmatization or exclusion of the person concerned. This includes for example data on gambling addiction, performances at school or at work or relational problems.
- User names, passwords and other login details. The possible impact on the data subjects will depend on the data processing and the nature of the personal data that these login details give access to. When assessing the impact one should consider that many people reuse passwords for different applications.
- Data which can be misused for (identity) fraud. This includes biometric data, copies of identity documents and the Citizens Service Number (CSN).
Other factors, such as the amount of exposed personal data per person or the number of data subjects whose personal data have been affected, may be a reason to report the data breach.
The data breach needs to be reported without undue delay and if possible, no later than 72 hours after the discovery of the data breach. For this purpose, a web form is available on the Dutch Data Protection Authority website. Reports can later be supplemented or withdrawn via this web form.
Notification of the data subject
In case of a data breach the affected subjects should be informed. The law requires that the data breach be reported to the person concerned without delay, so that they can take measures to protect themselves against potential consequences of the data breach. The sooner the person concerned is informed, the sooner they can act.
If the compromised data is incomprehensible or inaccessible to unauthorized persons by for example encryption or hashing, then the data subject need not be notified. In this case, there will be no adverse consequences for the data subject.
Reporting to data subjects can be done by posting a message on the website of CDD Solutions and/or by sending an email or letter to those involved. The notification should contain the following information:
- The nature of the infringement
- The cause of the data breach
- A description of the leaked personal data
- Any measures that have been or are being taken to close the data breach
- An assessment of the risk that those involved may run
- The contact details of CDD Solutions
Part 2: Standard Clauses for Data Processing
Along with the Data Pro Statement, these standard clauses constitute the data processing agreement. They also constitute an annex to the Agreement and to the appendices to this Agreement, e.g. any general terms and conditions which may apply.
Article 1. Definitions
The following terms have the following meanings ascribed to them in the present Standard Clauses for Data Processing, in the Data Pro Statement and in the Agreement:
- 1.1 Dutch Data Protection Authority (AP): the supervisory authority defined in Section 4.21 of the GDPR.
- 1.2 GDPR: the General Data Protection Regulation.
- 1.3 Data Processor: the party which, in its capacity as an ICT supplier, processes Personal Data on behalf of its Client as part of the performance of the Agreement.
- 1.4 Data Pro Statement: a statement issued by the Data Processor in which it provides information such as the intended use of its products and/or services, any security measures which have been implemented, sub-processors, data breach, certification and dealing with the rights of Data Subjects.
- 1.5 Data Subject: a natural person who can be identified, directly or indirectly.
- 1.6 Client: the party on whose behalf Data Processor processes Personal Data. Client can either be the controller (the party who determines the purpose and means of the processing) or another data processor.
- 1.7 Agreement: the agreement concluded between Client and Data Processor, based on which the ICT supplier provides services and/or products to Client, the data processing agreement forming part of this agreement.
- 1.8 Personal Data: any and all information regarding a natural person who has been or can be identified, as defined in Article 4.1 of the GDPR, processed by Data Processor to meet its requirements under the Agreement.
- 1.9 Data Processing Agreement: the present Standard Clauses for Data Processing , which, together with Data Processor's Data Pro Statement (or similar such information), constitute the data processing agreement within the meaning of Article 28.3 of the GDPR.
Article 2. General provisions
- 2.1 The present Standard Clauses for Data Processing apply to all Personal Data processing operations carried out by Data Processor in providing its products and services, as well as to all Agreements and offers. The applicability of Client's data processing agreements is explicitly rejected.
- 2.2 The Data Pro Statement, and particularly the security measures described in it, may be adapted from time to time to changing circumstances by Data Processor. Data Processor shall notify Client in the event of significant revisions. If Client in all reasonableness cannot agree to the revisions, Client shall be entitled to terminate the data processing agreement in writing, stating its reasons for doing so, within thirty days of having been served notice of the revisions.
- 2.3 Data Processor shall process the Personal Data on behalf of Client, in accordance with the written instructions provided by Client and accepted by Data Processor.
- 2.4 Client or its customer shall serve as the controller within the meaning of the GDPR, shall have control over the processing of the Personal Data and shall determine the purpose and means of processing the Personal Data.
- 2.5 Data Processor shall serve as the processor within the meaning of the GDPR and shall therefore not determine the purpose and means of processing the Personal Data, and shall not make any decisions on the use of the Personal Data and other such matters.
- 2.6 Data Processor shall implement the GDPR as laid down in the present Standard Clauses for Data Processing, the Data Pro Statement and the Agreement. It is up to Client to assess, on the basis of this information, whether Data Processor is providing sufficient guarantees with regard to the implementation of appropriate technical and organisational measures in order to ensure that the processing operations meet the requirements of the GDPR and that Data Subjects' rights are sufficiently protected.
- 2.7 Client shall guarantee Data Processor that it acts in accordance with the GDPR, that it provides a high level of protection for its systems and infrastructure at all time, that the nature, use and/or processing of the Personal Data are not unlawful and that they do not violate any third party's rights.
- 2.8 Administrative fines imposed on Client by the Dutch Data Protection Authority cannot be recovered from Data Processor.
Article 3. Security
- 3.1 Data Processor shall implement the technical and organisational security measures set out in its Data Pro Statement. In implementing the technical and organisational security measures, Data Processor shall take into account the state of the art and the costs of implementation, as well as the nature, scope, context and purposes of the processing and the intended use of its products and services, and the risk in processing the data of varying likelihood and severity inherent to the rights and freedoms of Data Subjects that are to be expected considering the nature of the intended use of Data Processor's products and services.
- 3.2 Unless explicitly stated otherwise in the Data Pro Statement, the products and services provided by Data Processor shall not be equipped to process special categories of personal data or data relating to criminal convictions and offences.
- 3.3 Data Processor seeks to ensure that the security measures it shall implement are appropriate for the manner in which Data Processor intends to use the products and services.
- 3.4 In Client's opinion, said security measures provide a level of security that is tailored to the risk inherent in the processing of the Personal Data used or provided by Client, taking into account the factors referred to in Article 3.1.
- 3.5 Data Processor shall be entitled to adjust the security measures it has implemented if to its discretion such is necessary for a continued provision of an appropriate level of security. Data Processor shall record any significant adjustments it chooses to make, e.g. in a revised Data Pro Statement, and shall notify Client of said adjustments where relevant.
- 3.6 Client may request Data Processor to implement further security measures. Data Processor shall not be obliged to honour such requests to adjust its security measures. If Data Processor makes any adjustments to its security measures at Client's request, Data Processor is entitled to invoice Client for the costs associated with said adjustments. Data Processor shall not be required to actually implement the requested security measures until both Parties have agreed upon them in writing. .
Article 4. Data breaches
- 4.1 Data Processor does not guarantee that its security measures shall be effective under all circumstances. If Data Processor discovers a data breach within the meaning of Article 4 sub 12 of the GDPR, it shall notify Client without undue delay. The "Data Breach Protocol" section of the Data Pro Statement outlines the way in which Data Processor shall notify Client of data breaches.
- 4.2 It is up to the Controller (the Client or its customer) to assess whether the data breach of which Data Processor has notified the Controller must be reported to the Dutch Data Protection Authority or to the Data Subject concerned. The Controller (Client or its customer) shall at all times remain responsible for reporting data breaches which must be reported to the Dutch Data Protection Authority and/or Data Subjects pursuant to Articles 33 and 34 of the GDPR. Data Processor is not obliged to report data breaches to the Dutch Data Protection Authority and/or to the Data Subject.
- 4.3 Where necessary, Data Processor shall provide further information on the data breach and shall assist Client to meet its breach notification requirements within the meaning of Articles 33 and 34 of the GDPR by providing all the necessary information available to Data Processor.
- 4.4 If Data Processor incurs any reasonable costs in doing so, it is entitled invoice Client for these, at the rates applicable at the time.
Article 5. Confidentiality
- 5.1 Data Processor shall ensure that the persons processing Personal Data acting under its authority have committed themselves to confidentiality.
- 5.2 Data Processor shall be entitled to provide third parties with Personal Data if and insofar as such is necessary due to a court order, statutory provision or order issued by a competent government authority.
- 5.3 Any and all access and/or identification codes, certificates, information regarding access and/or password policies provided by Data Processor to Client, and any and all information provided by Data Processor to Client detailing the technical and organisational security measures included in the Data Pro Statement are confidential and shall be treated as such by Client and shall only be disclosed to authorised employees of Client. Client shall ensure that its employees comply with the requirements described in this article.
Article 6. Term and termination
- 6.1 This data processing agreement constitutes part of the Agreement, and any new or subsequent agreement arising from it and shall enter into force at the time of the conclusion of the Agreement and shall remain effective for an indefinite period.
- 6.2 This data processing agreement shall end by operation of law upon termination of the Agreement or upon termination of any new or subsequent agreement arising from it between parties.
- 6.3 If the data processing agreement is terminated, Data Processor shall delete all Personal Data it currently stores and which it has obtained from Client within the timeframe laid down in the Data Pro Statement, in such a way that the Personal Data can no longer be used and shall have been rendered inaccessible. Alternatively, if such has been agreed, Data Processor shall return the Personal Data to Client in a machine-readable format.
- 6.4 If Data Processor incurs any costs associated with the provisions of Article 6.3, it shall be entitled to invoice Client for said costs. Further arrangements relating to this subject can be laid down in the Data Pro Statement.
- 6.5 The provisions of Article 6.3 do not apply if Data Processor is prevented from removing or returning the Personal Data in full or in part by a statutory provision. In such instances, Data Processor shall only continue to process the Personal Data insofar as such is necessary by virtue of its statutory obligations. Furthermore, the provisions of Article 6.3 shall not apply if Data Processor is the Controller of the Personal Data within the meaning of the GDPR.
Article 7. The rights of Data Subjects, Data Protection Impact Assessments (DPIA) and auditing rights
- 7.1 Where possible, Data Processor shall cooperate with reasonable requests made by Client relating to Data Subjects who invoke their rights from Client. If Data Processor is directly approached by a Data Subject, it shall refer the Data Subject to Client where possible.
- 7.2 If Client is required to carry out a Data Protection Impact Assessment or a subsequent consultation within the meaning of Articles 35 and 36 of the GDPR, Data Processor shall cooperate with such, following a reasonable request to do so.
- 7.3 Data Processor shall be able to demonstrate its compliance with its requirements under the data processing agreement by means of a valid Data Processing Certificate or an equivalent certificate or audit report (third-party memorandum) issued by an independent expert.
- 7.4 In addition, at Client's request, Data Processor shall provide all other information that is reasonably required to demonstrate compliance with the arrangements made in this data processing agreement. If, in spite of the foregoing, Client has grounds to believe that the Personal Data are not processed in accordance with the data processing agreement, Client shall be entitled to have an audit performed (at its own expense) not more than once every year by an independent, certified, external expert who has demonstrable experience with the type of data processing operations carried out under the Agreement. The scope of the audit shall be limited to verifying that Data Processor is complying with the arrangements made regarding the processing of the Personal Data as set forth in the present data processing agreement. The expert shall be subject to a duty of confidentiality with regard to his/her findings and shall only notify Client of matters which cause Data Processor to fail to comply with its obligations under the data processing agreement. The expert shall furnish Data Processor with a copy of his/her report. Data Processor shall be entitled to reject an audit or instruction issued by the expert if to its discretion the audit or instruction is inconsistent with the GDPR or any other law, or that it constitutes an unacceptable breach of the security measures it has implemented.
- 7.5 The parties shall consult each other on the findings of the report at their earliest convenience. The parties shall implement the measures for improvement suggested in the report insofar as they can be reasonably expected to do so. Data Processor shall implement the proposed measures for improvement insofar as to its discretion such are appropriate, taking into account the processing risks associated with its product or service, the state of the art, the costs of implementation, the market in which it operates, and the intended use of the product or service.
- 7.6 Data Processor shall be entitled to invoice Client for any costs it incurs in implementing the measures referred to in this article.
Article 8. Sub-processors
- 8.1 Data Processor has specified in the Data Pro Statement whether Data Processor uses any third parties (subprocessors) to help it process the Personal Data, and if so, which third parties.
- 8.2 Client hereby authorises Data Processor to hire other sub-processors to meet its obligations under the Agreement.
- 8.3 Data Processor shall notify Client of any changes concerning the addition or replacement of the third parties (sub-processors) hired by Data Processor, e.g. through a revised Data Pro Statement. Client shall be entitled to object to such changes . Data Processor shall ensure that any third parties it hires shall commit to ensuring the same level of Personal Data protection as the security level Data Processor is bound to provide to the Client pursuant to the Data Pro Statement.
Article 9. Other provisions
These Standard Clauses for Data Processing, along with the Data Pro Statement, constitute an integral part of the Agreement. Therefore, any and all rights and obligations arising from the Agreement, including any applicable general terms and conditions and/or limitations of liability, shall also apply to the data processing agreement.